Now that the core parts of the network is set up, we can set up a VPN server to allow connectivity to the home network while travelling. Conveniently, OPNsense provides a Wireguard service.
Static entrypoint
Before we can set up the VPN server, we need a static IP address or hostname which we can configure clients to connect to. If you have a static IP already, you can simply use that, or in my case, I use a dynamic DNS service with a custom domain. OPNsense also provides a dynamic DNS plugin os-ddclient that supports many providers.
Wireguard
Create instance
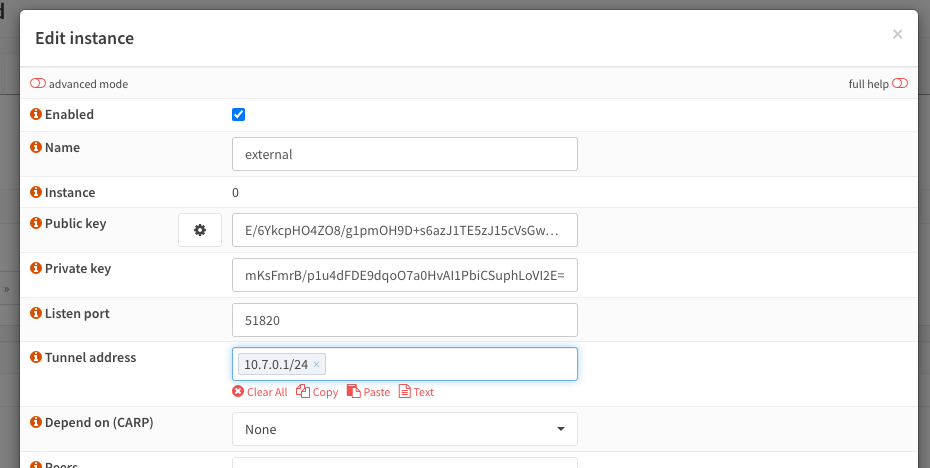
Under VPN > Wireguard, create a new instance. Give the instance a name, generate a key pair and set the tunnel address. The tunnel address is the LAN IP address of the Wireguard tunnel itself. This will be a private subnet, and can be thought of as the router IP for clients on the VPN subnet. The default used by Wireguard is 10.7.0.1/24. This is find for my use case so I will use that.
Once the configuration is saved, restart Wireguard by enabling/disabling to apply the changes.
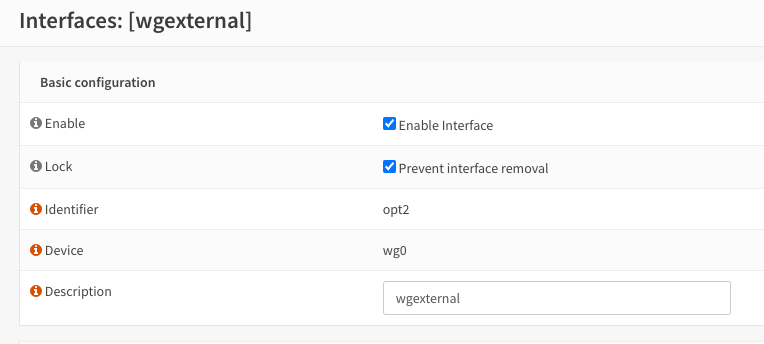
Assign interface
A new device will be created named wg0. Go to Interfaces > Assignments and assign the new interface by selecting the wg0 device and adding a descriptive name. Once saved, a new entry with the name will appear under Interfaces > [Interface Name]. Enable this interface by checking the box.
Generate peers
The Wireguard plugin provides a convenient peer generator that makes it very easy to add clients by text configuration or QR code. There are really only three settings that are important:
- Endpoint - This is the external address that clients will use to connect. Assuming you are using the default port, this will be the hostname or static IP address with port 51820.
- Allowed IPs - Specify a list of comma separated subnets that clients are allowed to access. For example if clients are only allowed to access the VPN subnet, this can be
10.7.0.0/24; if the client is to forward all traffic through Wireguard, this can be0.0.0.0/0,::/0. - The DNS used by clients will be set to the tunnel address (
10.7.0.1), which will use system resolvers. This can be overridden in the “DNS Servers” field.
Remember to restart Wireguard after modifying the client list.